wardmundy
Nerd Uno
- Joined
- Oct 12, 2007
- Messages
- 19,204
- Reaction score
- 5,225
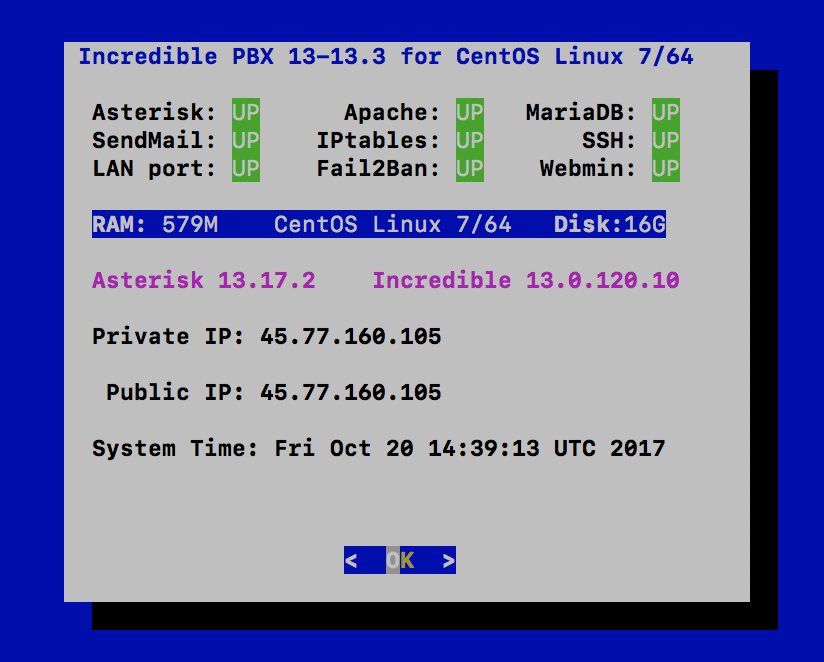
PIONEERS: I think we're ready for a few brave souls. What you get: Asterisk 13.17.2 with the latest open source FreePBX 13 GPL modules. No commercial modules.
DISCLAIMERS:
1. This should be considered ALPHA code and should not be used in production environments. DO NOT RUN WITHOUT THE PRECONFIGURED TRAVELIN' MAN 3 FIREWALL WHICH IS INSTALLED AND CONFIGURED BY DEFAULT.
2. This has only been tested with a minimal install of 64-bit CentOS 6.9 and 7. 32-bit is not yet supported.CentOS 7 installs currently fail. Incredible Fax reportedly broken now fixed.
3. SIP ports have changed. Chan_SIP is now default at UDP 5060. PJsip is UDP 5061.
4. This is the LEAN version of Incredible PBX to get the kinks ironed out. No Incredible PBX apps or preconfigured extensions, trunks, routes are provided.
5. There probably will NOT be an upgrade path from previous releases of Incredible PBX, and you will not be able to use your settings in this version to move to the full Incredible PBX implementation of Incredible PBX 13-13 at a later date.
6. Google Voice plain text and OAuth 2 passwords are supported. OAuth2 has been tested and works fine. Same code as in previous Incredible 13-12 releases so plain text should also work with the usual caveats covered in the NV tutorials.
7. A module repository isnot yet now in place for updates or adding new modules using Module Admin. If you delete a module, it's gone permanently in this build.
8. If you need a particular module that is not included, let us know and we'll add it in next build. GPL modules can also be added from GitHub. Tutorial here. NOTE: Be sure to modify script to access FreePBX 13 GPL modules instead of FreePBX 12!!!
9. FreePBX module signature checking has been turned off, and error messages will not display on the Dashboard, i.e. no critical issues will ever be found whether they exist or not. Hence the reason you need your firewall to protect your server.
10. Feedback encouraged. Just post a note in this thread.
INSTALLATION:
1. Begin by installing 64-bit, CentOS 6.9 minimal.
2. Login as root and download and untar the Incredible PBX installer.
3. If you're on a low-memory (under 1GB) platform, run the script to create a swapfile:
4. Kick off the install:
5. After CentOS is brought up to specs for Incredible PBX, your server will reboot.
6. Log back into your server as root, and run the installer a second time. Be sure SSH/Putty window is at least 85 x 25, or Asterisk compile may fail!!!
7. Reboot.
8. Set your admin password for web GUI access:
9. Use a browser to login to the GUI as admin at your server's IP address and begin your adventure.
DISCLAIMERS:
1. This should be considered ALPHA code and should not be used in production environments. DO NOT RUN WITHOUT THE PRECONFIGURED TRAVELIN' MAN 3 FIREWALL WHICH IS INSTALLED AND CONFIGURED BY DEFAULT.
2. This has only been tested with a minimal install of 64-bit CentOS 6.9 and 7. 32-bit is not yet supported.
3. SIP ports have changed. Chan_SIP is now default at UDP 5060. PJsip is UDP 5061.
4. This is the LEAN version of Incredible PBX to get the kinks ironed out. No Incredible PBX apps or preconfigured extensions, trunks, routes are provided.
5. There probably will NOT be an upgrade path from previous releases of Incredible PBX, and you will not be able to use your settings in this version to move to the full Incredible PBX implementation of Incredible PBX 13-13 at a later date.
6. Google Voice plain text and OAuth 2 passwords are supported. OAuth2 has been tested and works fine. Same code as in previous Incredible 13-12 releases so plain text should also work with the usual caveats covered in the NV tutorials.
7. A module repository is
8. If you need a particular module that is not included, let us know and we'll add it in next build. GPL modules can also be added from GitHub. Tutorial here. NOTE: Be sure to modify script to access FreePBX 13 GPL modules instead of FreePBX 12!!!
9. FreePBX module signature checking has been turned off, and error messages will not display on the Dashboard, i.e. no critical issues will ever be found whether they exist or not. Hence the reason you need your firewall to protect your server.
10. Feedback encouraged. Just post a note in this thread.
INSTALLATION:
1. Begin by installing 64-bit, CentOS 6.9 minimal.
2. Login as root and download and untar the Incredible PBX installer.
Code:
cd /root
yum -y install net-tools nano wget tar
wget http://incrediblepbx.com/incrediblepbx-13-13-LEAN.tar.gz
tar zxvf incrediblepbx-13-13-LEAN.tar.gz
rm -f incrediblepbx-13-13-LEAN.tar.gz3. If you're on a low-memory (under 1GB) platform, run the script to create a swapfile:
Code:
./create-swapfile-DO4. Kick off the install:
Code:
./IncrediblePBX-13-13.sh5. After CentOS is brought up to specs for Incredible PBX, your server will reboot.
6. Log back into your server as root, and run the installer a second time. Be sure SSH/Putty window is at least 85 x 25, or Asterisk compile may fail!!!
Code:
./IncrediblePBX-13-13.sh7. Reboot.
8. Set your admin password for web GUI access:
Code:
/root/admin-pw-change9. Use a browser to login to the GUI as admin at your server's IP address and begin your adventure.

Last edited: